Readykey systems are designed for simple administration. A front panel display, keypad and reader provide all access control functions while an attached printer can print transaction records as well as listings of personnel, system setup and past events.
Name your door for printing purposes; its identity will appear on all reports printed.
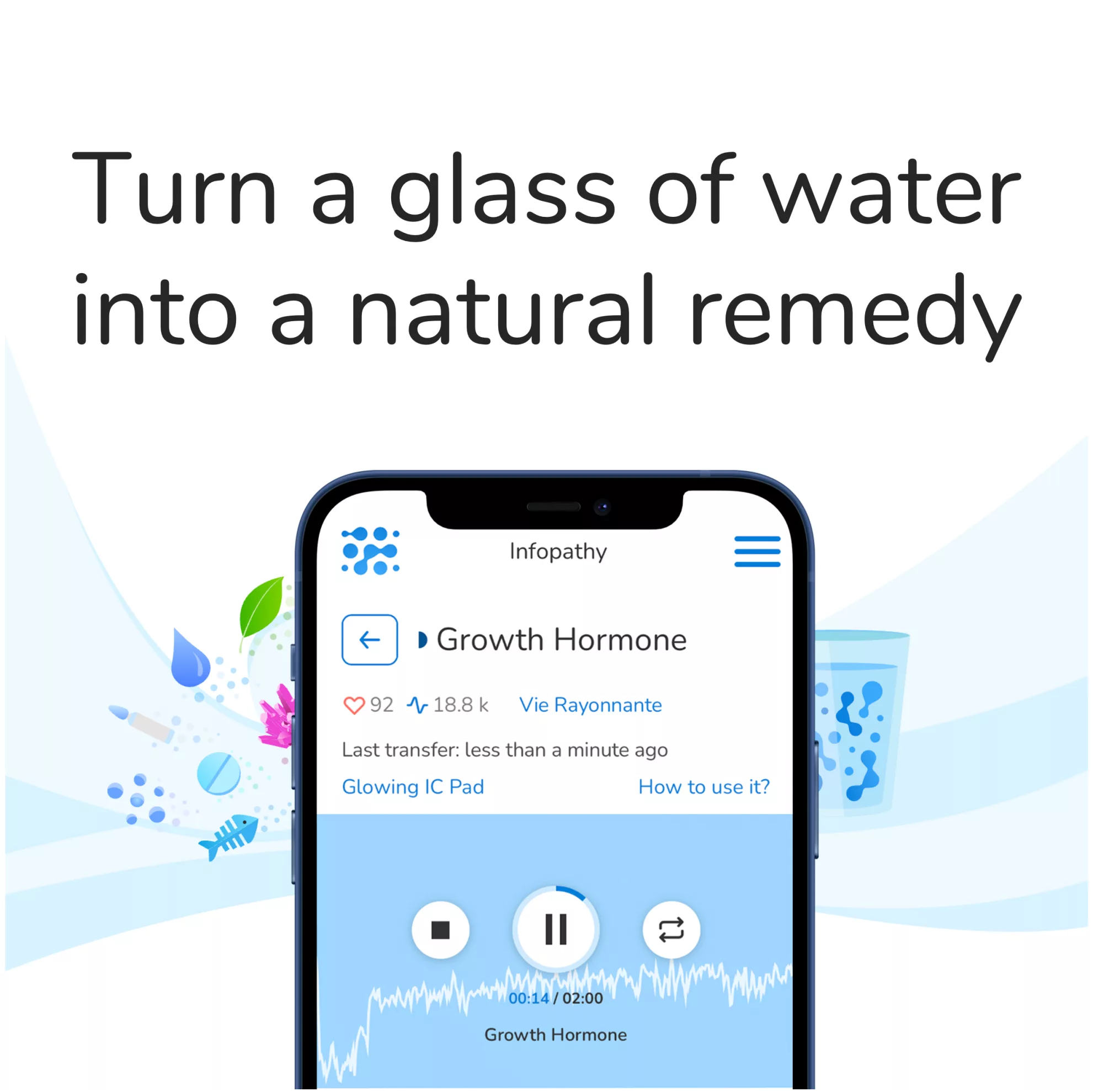
RISSC® Information Security System for Computers
The RISC-V instruction set architecture was created with security in mind. Its customizable features enable designers to add security mechanisms that span across a broad spectrum of applications and market segments, from microcontrollers to HPC. This includes vaults, roots of trust and IP blocks – which should all be added early on during design processes for optimal security results.
RISC-V ISA provides multiple privilege modes: user mode, supervisor mode and machine mode. Each of these has different privilege levels that can be enforced through separate hardware and software protection mechanisms – for instance a security vault could prevent untrusted code from running except through its root of trust mode while its counterpart could block access to memory regions which require trusted execution.
Memory safety in RISC-V cores can be enhanced further through the inclusion of memory-protection metadata. This data identifies which areas of memory can be accessed through particular operations and stores it inline with addresses; by comparing an operation’s tag bit with this metadata, computers can detect cases when programs attempt to read or write outside their bounds.
Physical Memory Protect (PMP) provides another means of memory protection. This method works by expanding RISC-V ISA with hardware extensions that restrict access to specific portions of memory by both software and hardware; this prevents malicious programs from accessing protected data while blocking legitimate software accessing it.
The K2100/K1100 door controllers support the RISC-V PMP extension by employing an additional processor to verify memory reads or writes. Unlike its main chip counterpart, however, this processor cannot access sensitive system information; hence it only has access to memory within the door controller, rather than alarm configuration information or customer-added personnel records or Time Profiles.
K2100/K1100 Door Controllers
The K2100/K1100 door controllers allow 16 doors to be controlled simultaneously while up to 4000 personnel can be administered through administration based on keypad, display, reader and networked printer reports of personnel setup, past events etc. One door controller acts as the Master while three other controllers act as Slaves; all communication and administration takes place through this central point – Slaves do not feature keyboards or displays of their own, however they respond to commands sent from Master.
The RISSC(r) Alarm Event Manager (K2015A) is an optional device designed to facilitate monitoring up to 8 inputs and provide up to 8 relay outputs, connected between a Master Door Controller and reader. When attached with compatible readers, its administration can be managed either through Readykey for Windows or by direct management from within its associated controller.
ReadykeyPRO, powered by Microsoft Windows 2000 Server, offers unparalleled scalability and flexibility. This system makes integration with Radionics‘ D7412G or D9412G Security Systems or third-party devices such as CCTV easy – plus wide area networks allow control across multiple locations and geographies.
Expandable, Flexible, and Global
ReadykeyPRO’s system was designed with standard components and interfaces in mind. As such, expansion should be easily, rapidly, and cost effectively achieved without costly hardware upgrades or reconfiguration. Instead of maintaining one centralized database per site for optimal efficiency, readykeyPRO maintains separate databases per individual site for increased efficiency.
ReadykeyPRO can be installed as either an independent access control system, or upgraded into your existing Stanley PAC system to include access control capabilities. A PAC 500 Retrofit Kit can help you convert existing K2000-series controllers to new PAC 500 controllers while maintaining power supply, readers, cabling and data in your existing enclosure – thus protecting investment value while optimizing legacy infrastructure value. It also enables data migration from K2000 controllers in order to take advantage of software features available with PAC 500 software solutions.